Best practices for secure identity and access management in K–12 schools
Every school day begins with a challenge: ensuring that every student and teacher has secure and easy access to the digital tools they need. As our schools become increasingly tech-savvy spaces, managing digital identities gets trickier—leading to security risks and operational hiccups.
From juggling the vast digital landscapes of modern edtech to addressing the rapid turnover of users each academic year, the necessity for robust Identity and Access Management (IAM) systems in schools has never been more apparent.
This article explores these challenges in depth and offers actionable best practices that can transform how schools handle digital identity, making security a seamless part of the educational process rather than a barrier.
| Key Takeaways |
| IAM systems streamline the management of digital identities, significantly reducing operational bottlenecks and enhancing the security of the educational process. Even though schools face multiple cybersecurity challenges that complicate the secure management of access and identity, effective IAM practices can help overcome them. Adopting comprehensive IAM best practices is key to safeguarding against unauthorized access and potential data breaches. |
Challenges of implementing secure IAM in schools
As edtech becomes increasingly useful to teaching and learning, more and more schools are ramping up their cybersecurity measures. One way they are doing this is through IAM systems. These systems help manage digital identities and access permissions, safeguarding against unauthorized access and potential breaches.
However, the challenge is not just to implement robust protections but to do so without disrupting time intended for learning. When K-12 schools try to implement this technology, they often encounter several persistent obstacles:
- Complex digital landscapes: Schools with access to digital tools, require not just students, teachers, and staff but also parents and guardians to access numerous digital accounts and applications. Managing these identities and access permissions across such a broad user base is complex and increases the potential for security breaches.
- Password management issues: Creating and distributing strong, randomized passwords manually is impractical. Many schools use simple password formulas to ease access, which, while convenient, opens up significant security gaps and makes accounts easier to compromise.
- Frequent user turnover: Constant changes in school rosters complicate access management. IT leaders often use spreadsheets to track these changes, but updates can be overlooked, leading to incorrect or missed access to critical tools.
- Limited IT resources: Many schools have small IT teams responsible for managing extensive technology infrastructures, including IAM systems. This often results in a lot of manual work and can stretch IT professionals thin. (Read: Implementing school security tools with a team of one)
- MFA compatibility: Most Multi-Factor Authentication (MFA) systems are designed for businesses and do not fit well in educational settings. This can result in MFA solutions that are inappropriate for classrooms, lack age-appropriate second factors, and lack the necessary troubleshooting tools for teachers.
- Implementation costs: Implementing advanced IAM systems, including MFA, can be expensive. The costs associated with purchasing, deploying, and managing these systems often exceed the budgets of many underfunded districts, creating a significant barrier to enhancing security infrastructure.
Despite the hurdles schools face, they are not insurmountable. Advances in technology and strategic planning offer a path forward that can align security with educational goals without undue disruption.
IAM best practices to protect your students
Implementing a robust IAM system is essential for protecting the digital identities of students and staff in K-12 schools. Below, we cover six key components for the successful implementation of IAM.
1. Single-sign on (SSO)
Single-sign on (SSO) allows users to access multiple applications with a single set of login credentials, making the entire process more efficient. By streamlining the authentication process, SSO enhances the educational experience by:
- Decreasing common password issues like lockouts or resets that disrupt classes.
- Improving user experience by reducing password fatigue.
- Increasing security by enforcing strong password policies.
- Centralizing access control, which makes it easier for administrators to manage user rights from one location.
- Reducing risks of unauthorized access by avoiding the need to share credentials across applications.
At Clever, our SSO solution is specifically designed to make this process as simple as possible for every user, regardless of age or technical proficiency. Users have the option to enter their username and password or they can use a Clever Badge—ideal for younger students who may struggle with passwords. These badges allow for secure login via a simple scan.
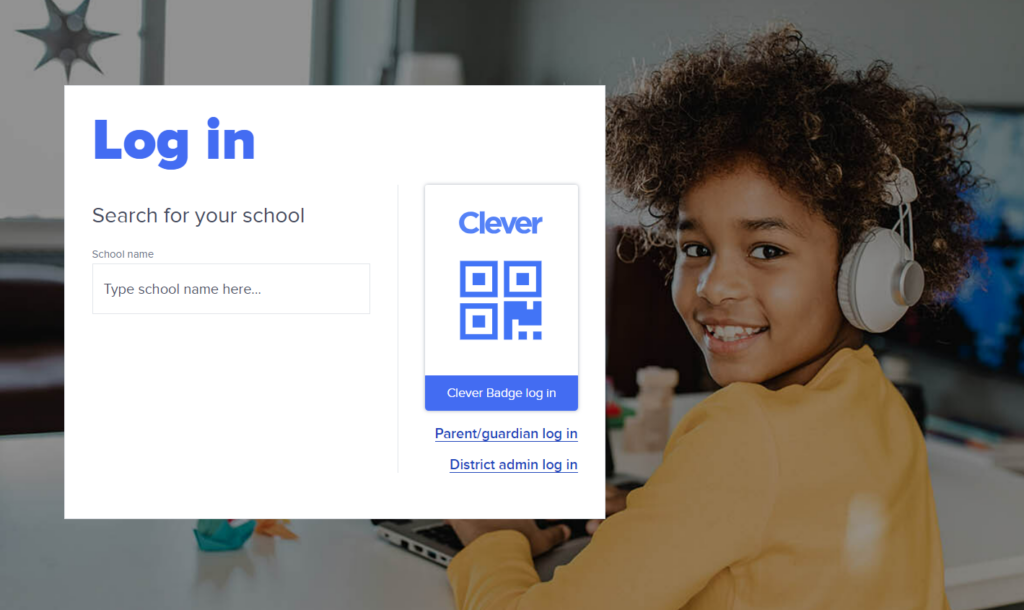
Once logged in, users are directed to a personalized portal where all their applications and resources are organized and readily accessible. This personalization ensures that each user’s most needed tools are right at their fingertips, tailored to their educational needs and roles.
Additionally, Clever’s SSO integrates seamlessly with your district’s Student Information Systems (SIS) and Learning Management Systems (LMS). This ensures that records and permissions are always up-to-date and secure, maintaining relevance and alignment with each user’s educational progression.
2. Multi-factor authentication (MFA)
Multi-factor authentication (MFA) adds an extra layer of security to the login process. It requires users to provide two or more forms of authentication before gaining access to sensitive resources or systems. This helps ensure that the person trying to gain access is who they claim to be.
Typically, users have to combine something they know (like a password), something they have (like a smartphone app or security token), and/or something they are (like a fingerprint or other biometric factor). This combination:
- Makes it much harder for attackers to gain access without possessing the second authentication factor.
- Enhances security by adding an additional verification step.
- Reduces the impact of compromised passwords.
- Increases confidence in digital security among students, staff, and parents.
Unlike generic MFA solutions that might not fit well with the needs of younger users or classroom environments, Clever’s Classroom MFA includes second factors that are age-appropriate and easy for students to use. For example, younger students may use a login picture in which they must select their animal, then their food from a group of randomized pictures each time they login as their secondary factor.
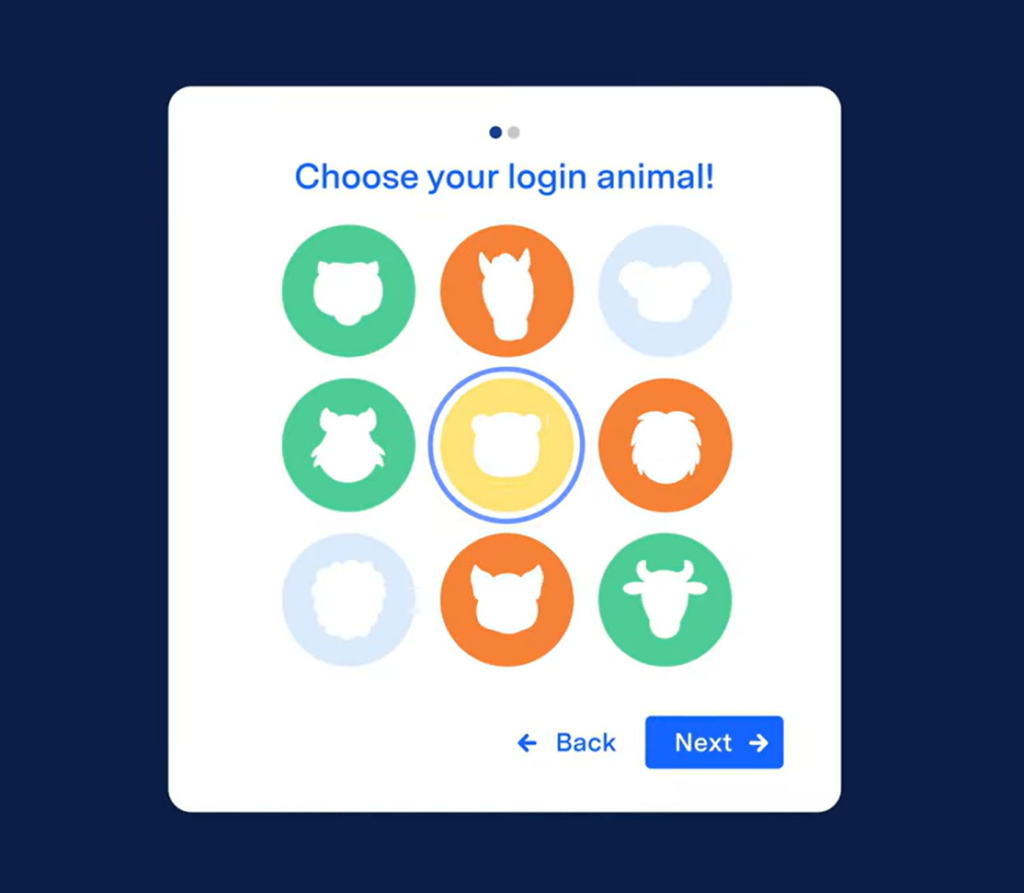
Teachers can also manage security measures within the classroom using delegated administration functionality. This prevents MFA from interfering with teaching and learning.
It also seamlessly integrates with the Clever SSO system, providing a smooth and secure user experience without complicating the login process. No matter where or what device students and teachers need to log in from, they can do so safely and efficiently.
Learn more about Clever Classroom MFA.
3. Automated account provisioning and deprovisioning
Managing who gets access to what and when is a big part of keeping our school systems secure. That’s where automated account creation (provisioning) and archiving (deprovisioning) come into play.
This process ensures that the right people have the right access to the right resources at the right times, and, just as importantly, that access is removed when it is no longer needed. This is important because it:
- Provides immediate access to necessary educational and administrative resources.
- Prevents unauthorized access and minimizes the risk of potential data breaches.
- Reduces human error when managing access rights across multiple systems and apps.
Clever’s automated provisioning and deprovisioning functionalities are integral to our IDM solution. They are designed to work seamlessly with your school’s existing SIS (student information system) and even your HRIS (HR information System) ensuring that user data and permissions are consistently synchronized across all platforms.
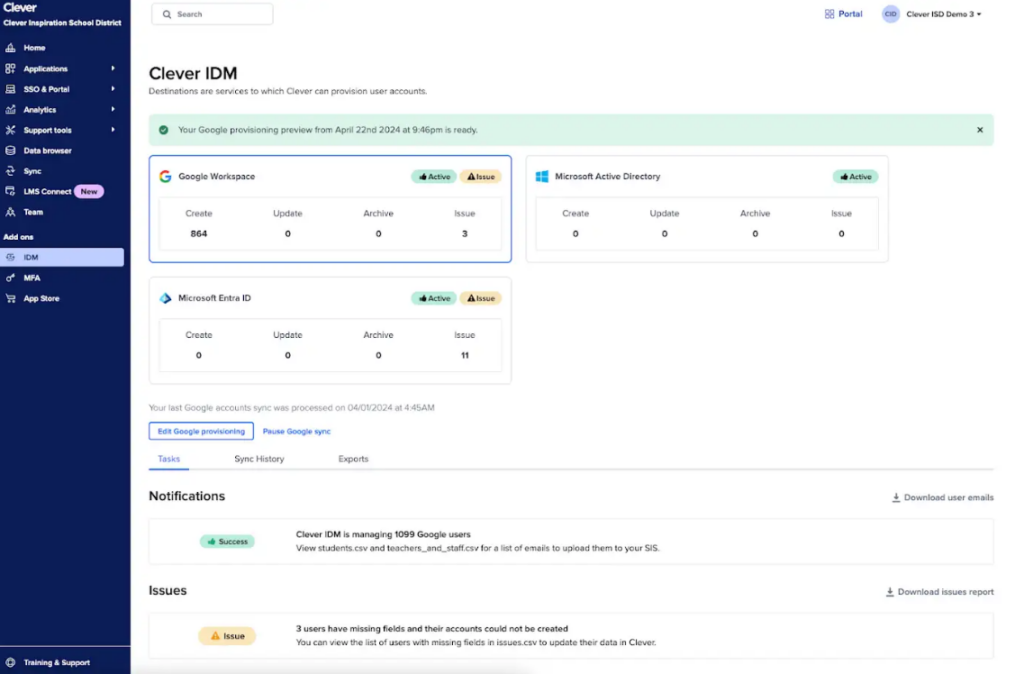
Whether it’s a student advancing to the next grade or a teacher moving to a new school, our system adjusts their access as needed, keeping everything up-to-date and secure.
This automation secures the digital environment and enhances the overall educational experience by ensuring that technological workflows are as interruption-free as possible.
Learn more about Clever IDM solutions.
4. Zero Trust security
Zero Trust is not about being paranoid; it’s about being prudent. It operates on a simple principle: never trust, always verify. This means no one gets access to anything inside our network without proper verification, regardless of whether they are inside or outside the school’s network.
In K-12 schools, where teachers, students, and staff access a variety of digital tools every day, Zero Trust ensures that:
- Every request for access is carefully verified to make sure it meets strict security standards before anyone is allowed in.
- Users only get access to the tools they need for their specific tasks.
- The school’s network is divided into smaller, secure sections, making it harder for any security issues to spread.
At Clever, we believe in a layered approach to security that supports the Zero trust practices. We integrate comprehensive identity verification and strict access controls at every point, making sure that the right people have the right access at the right times, and under the right conditions.
This approach extends across all our platforms, from the Clever Portal to each app integrated into our system.
5. Role-based access control (RBAC)
Role-Based Access Control (RBAC) is a security strategy based on the principle that not everyone needs access to all resources. Once a user is logged in and verified, RBAC ensures they gain access only to the resources necessary for their specific role—nothing more, nothing less.
It’s also important to regularly review and update these roles and permissions as things often change in school settings. For example, a teacher might take on additional duties such as becoming a club advisor, or a staff member might switch departments.
Keeping this targeted access control is particularly effective in maintaining security and operational efficiency within the school district. By assigning roles specific access rights, schools can minimize the risk of accidental or malicious breaches.
At Clever, we incorporate RBAC into our products to ensure that every user experience is optimized for security and functionality. Our system allows school administrators to easily assign roles, ensuring that changes in staff duties or student enrollments are quickly reflected in access rights.
This flexibility not only enhances security but also improves the overall educational experience by ensuring that all interactions with our technology are relevant and appropriate.
Learn more about our security practices.
6. Monitoring and auditing
Implementing IAM is only the start. To keep our schools safe, we need to continually watch over these systems and check them regularly. This vigilant approach ensures our implementations function correctly and remain secure against new threats.
Continuously monitoring and auditing are essential because they allow us to:
- Detect irregularities like unusual login attempts or accessing resources at odd hours.
- Address issues promptly, preventing potential problems from escalating.
- Reassure students, parents, and staff that their data is protected, reinforcing our commitment to security.
- Maintain detailed logs of system activity that help during audits, prove compliance, and aid in troubleshooting efficiently.
At Clever, our approach to monitoring and auditing is built into every layer of our platform. We provide tools that allow school administrators to easily review access logs and usage reports, giving them clear visibility into how resources are being used and by whom. This transparency is vital for fostering a secure educational environment.
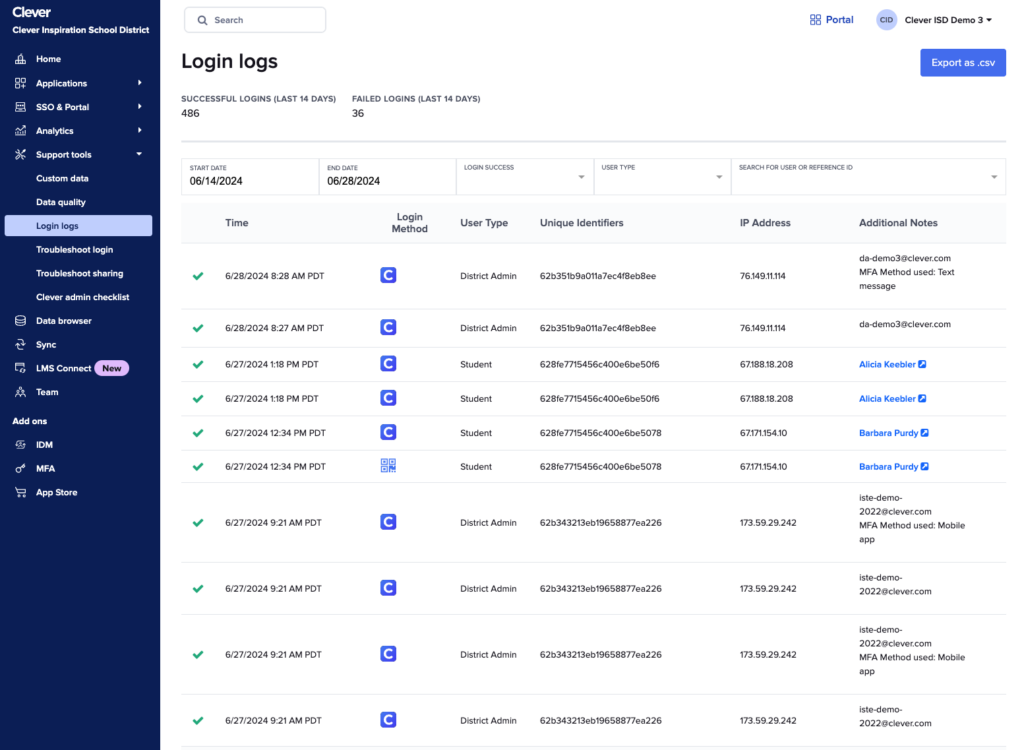
Moreover, our systems are designed to automatically flag activities that deviate from established patterns of normal behavior. This proactive stance on security ensures that potential issues are addressed before they can evolve into serious problems.
Stay ahead of the curve with Clever
As educational technology evolves, so do the challenges and opportunities in securing our digital environments. Clever’s Identity and Access Management (IAM) solutions are designed to meet these challenges head-on, providing robust, easy-to-use tools tailored specifically for the needs of K-12 schools. By choosing Clever, you’re not just keeping up with security trends; you’re staying ahead of them. Learn more about Clever’s IAM solutions and discover how we can help you build a safer, more efficient learning environment.

More to read
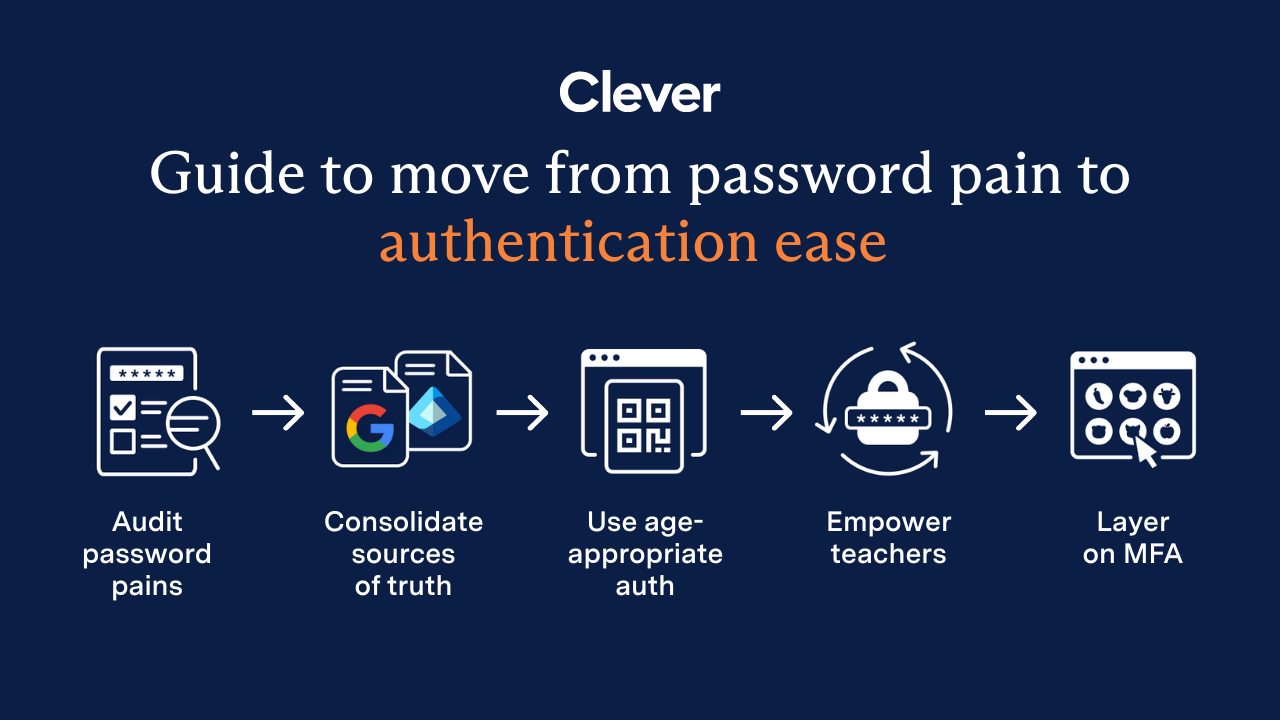
December 23, 2025
End password chaos: The 5-step guide to secure, age-appropriate logins in schoolsSchool IT departments — take these 5 steps to offload the burden of manual password resets while improving cybersecurity for classrooms.
December 10, 2025
Wonde vs. Clever: 2025 Side-by-Side ComparisonWhen it comes to choosing the right edtech platform for your school or trust, there’s a lot to consider. Can it sync reliably with your Management Information System (MIS)? Support secure logins for every user, on every device? Scale across multiple schools without overloading your IT team? Wonde and Clever are two of the most […]

October 21, 2025
Stop the Sticky Notes: Bend-La Pine’s Simple, Secure Fix for Substitute Teacher AccessRobbie Faith, an instructional technology coach at Bend-La Pine Schools, successfully implemented a Clever feature to streamline secure access to digital resources for short-term substitutes, leading to more effective sub planning for teachers, increased confidence for subs, and more consistent learning for students.


















