The Underestimated Threat: Why Student Accounts Are Targets for Cyberattacks
In the world of cybersecurity, student accounts are considered low risk because they are inside a digital walled garden. But this perception is not only outdated, it’s dangerous.
Recent data from a national cybersecurity survey of school leaders reveals that one in four school organizations have seen an increase in cyberattacks targeting student accounts. Despite this rising trend, only 5% of student accounts have multi-factor authentication (MFA)—a critical security measure that can prevent account takeover.
Rising Risks on Student Accounts
1 in 4
70%
5%
“We often took student accounts for granted,” said Mark Racine, former CIO of Boston Public Schools. “We thought, well, it’s just a student account—they don’t have access to very much. But that’s not always true. Misconfigurations, cloud sharing, and false assumptions about internal safety have created real vulnerabilities.”
Student account takeovers aren’t always harmless—and they’re happening more often. While many are internal incidents that lead to bullying, emotional harm, or lost IT hours, they’re usually limited in scale compared to external threats. But when threat actors from outside the school organization gain access—often by exploiting misconfigurations, credential reuse, or social engineering—these takeovers can become dangerous entry points into school systems.
In this article, we’ll walk through the anatomy of a school cyberattack, examine real-world incidents, and offer actionable strategies to help schools defend against these growing threats.
The Anatomy of a School Cyberattack: Three Core Stages
Not all cyberattacks look the same but research has identified these common patterns in attacks.
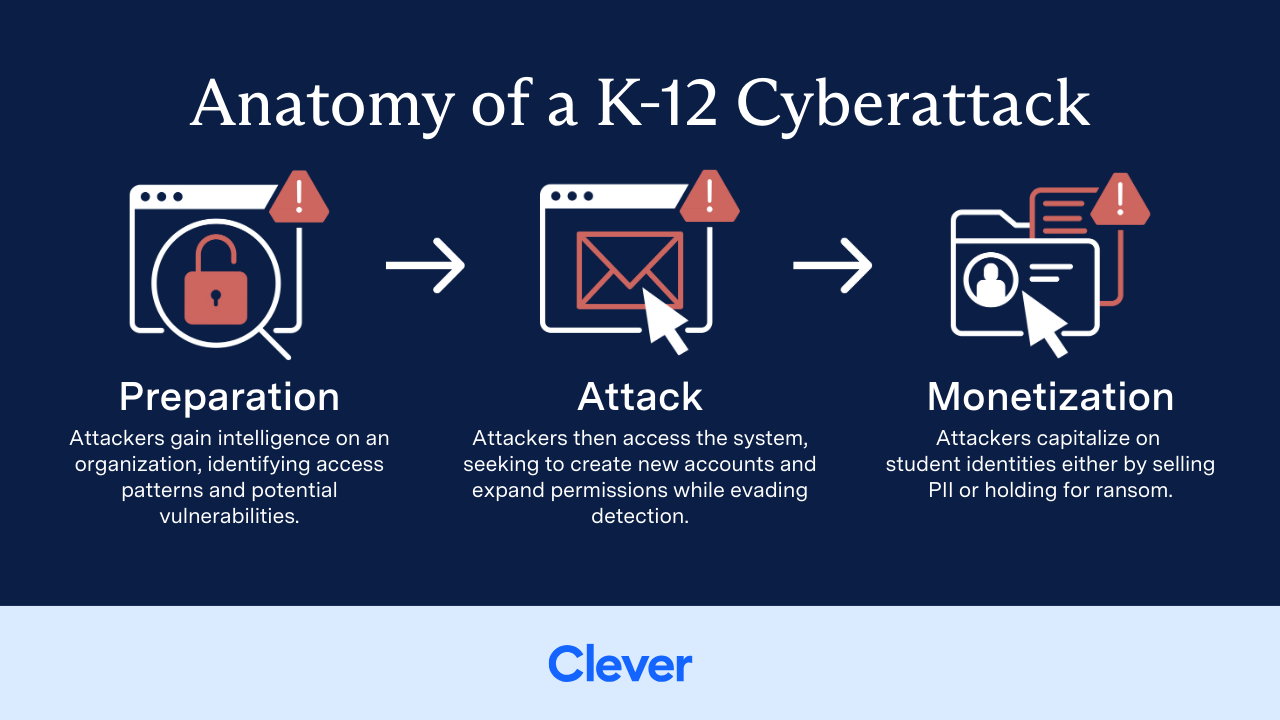
1. Preparation (Reconnaissance)
Before any attack is launched, there’s a reconnaissance phase. Threat actors gather intelligence on a school organization’s software stack, user access patterns, and potential vulnerabilities. In today’s landscape, this step has become disturbingly easy. Tools and services—many enhanced by generative AI—enable attackers to craft convincing phishing emails and probe for weak points with minimal effort.
They may pull student emails from the dark web, analyze school-organization-wide login credential patterns, and test default credentials, all without triggering significant alerts.
2. Attack (Exploitation & Expansion)
Armed with reconnaissance data, attackers move to the exploitation phase. Here, common methods include:
- Phishing campaigns that trick students into revealing or using their login credentials.
- Credential stuffing using reused passwords from other breached sites to try and successfully log in.
- Malware infections delivered through open cloud drives or weakly protected apps.
- Exploiting misconfigurations, such as overly permissive Google Groups or cloud storage sharing.
Once inside, attackers focus on escalating access, creating new accounts, or moving laterally across systems—sometimes without detection. This step is critical to be aware of because although student accounts themselves may have limited access to data, attackers may then leverage social engineering tactics or exploiting cloud sharing misconfigurations to gain access to much more.
3. Monetization (The Real Damage)
This final phase is where attackers capitalize on the intrusion. Student identities can be exfiltrated and sold. Sensitive documents (like IEPs) can be downloaded and used to ransom the school. And while some attackers are sophisticated, many operate with low-tech methods, relying on simplicity and misdirection rather than advanced code.
Real-World Scenarios: Lessons from Damaging Incidents
Now we know the essential patterns, let’s examine the stories of real attacks on schools to understand the potential impact of future attacks.
The Fake Internship Scam
This low-tech but highly effective scam began with a simple email: a fake remote internship opportunity, sent at just the right time in spring when students were searching for summer plans. The email didn’t contain any malicious links or files—just a prompt to reply for more information. Once students responded, the attacker moved the conversation to SMS, promised a $3,000 check to buy work equipment, and later asked for a partial refund once the fake check was deposited.
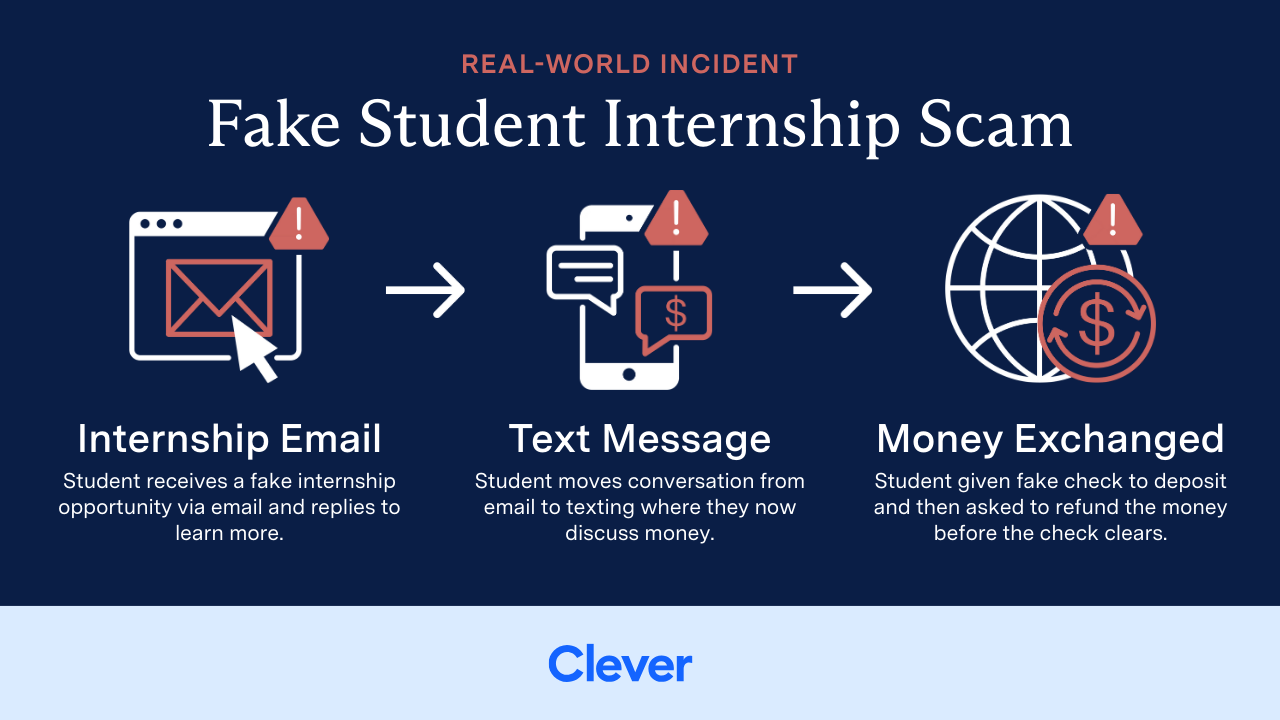
“This one scared us. It was incredibly low-tech—no credentials or code required. A teacher, thinking it was a real opportunity, even promoted it in Google Classroom. Suddenly, the whole class was involved.” – Mark Racine, former CIO of Boston Public Schools
The key lesson: even the most basic scams can spread quickly in trusted environments, making staff training and proactive communication just as important as technical defenses.
The Compromised Student Account
In another case, attackers used credential dumps to target student logins. Once inside, they probed cloud storage and communication platforms for vulnerabilities. In one school organization, they joined open Google Groups, accessing private discussions and documents—including sensitive student records.
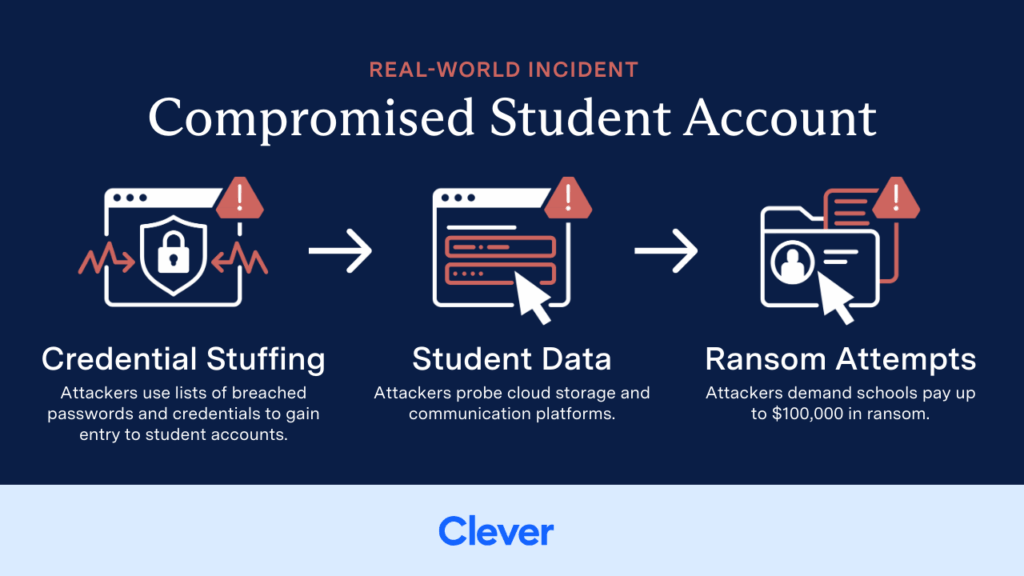
They attached compromised accounts to shared Drives, downloaded data, and attempted to ransom the school organization. While the target school avoided ransom, others hit by the same group were extorted for up to $100,000.
The key lesson: attackers don’t need admin credentials to do serious damage—student accounts often grant enough access to cause real harm.
Five Strategies for Risk Mitigation
Protecting against cyber threats isn’t just about using the right tools—it also means creating strong habits, clear systems, and shared expectations that make it harder for attackers to break in. These five strategies give schools simple, effective ways to lower risk and build a safer digital environment.
1. Develop and Run Awareness Campaigns
Build “group immunity” by training students, teachers, and even parents to spot suspicious activity. Tailor campaigns to known threats, reinforce safe behaviors, and frame students as responsible digital citizens. Awareness is your frontline defense—especially against social engineering. Including students in these awareness campaigns strengthen your community and can pay dividends into the future for all of us.
2. Assess and Refine Authentication Protocols
SSO and MFA should be standard for students and staff alike. While balancing usability for younger students is important, modern MFA solutions (like QR codes, passkeys, and pictograms) are increasingly student-friendly. Bringing students into these defensive practices reduces likelihood of takeovers. School organizations should make secure authentication a procurement requirement for all edtech tools.
3. Implement Least Privileged Access
Limit what student accounts can access by default. Review and reduce file-sharing settings, access permissions, and open group memberships. Students being part of your overall digital ecosystems requires you to have secure defaults for all sharing settings. A compromised account should never serve as a golden key to sensitive systems.
4. Establish Clear Communication Protocols
Defining how and where official communication happens within a school organization is one of the simplest—and most overlooked—ways to reduce risk. When school organizations lack a standardized way to share legitimate job postings, tech support info, or password reset notices, attackers can exploit the confusion.
Standardizing official communication reduces the success rate of phishing attempts and imposter messages by giving users a clear sense of what to expect—and what to question. Make sure you reinforce this in your training so students and other users know how to validate the legitimacy of communication.
5. Bonus Tips
If your school uses Google Workspace or Office 365, these extra steps can help strengthen your defenses and close common security gaps.
- Block legacy authentication & less secure apps
- Centralize access with a single identity provider.
- Use Google’s “target audiences” to restrict file sharing.
- Encourage strong passwords (12+ characters) or use managed passkeys.
Here’s a copy of the Google Workspace & Office 365 Tips to share with your team.
How Schools Can Be Proactive, Not Reactive to Cybersecurity Threats
It’s time to stop underestimating student accounts but include them in our security posture to enhance it.
They are gateways—sometimes to sensitive data, often to an entire school system’s digital ecosystem. Every compromised account is a potential breach. By raising awareness, strengthening authentication, enforcing access controls, and creating consistent communication channels, we can turn the tide.
The threats are evolving. So must our defenses.
Clever’s Role in Securing Student Accounts
At Clever, our mission is to connect every student to a world of learning—securely.
We partner with 110,000 schools around the world, providing a secure foundation for student identity and access. Our layered security includes robust password management, customizable MFA options, and adaptive controls tailored to grade level. Whether through tokens, passkeys, Badges, 6-digit PINs, or event login pictures for younger learners, we’re committed to making security accessible for all students.
Demo: Multi-factor authentication for students
Contact a Cybersecurity Specialist
Collects leads for cybersecurity products

More to read
December 23, 2025
End password chaos: The 5-step guide to secure, age-appropriate logins in schoolsSchool IT departments — take these 5 steps to offload the burden of manual password resets while improving cybersecurity for classrooms.
December 10, 2025
Wonde vs. Clever: 2025 Side-by-Side ComparisonWhen it comes to choosing the right edtech platform for your school or trust, there’s a lot to consider. Can it sync reliably with your Management Information System (MIS)? Support secure logins for every user, on every device? Scale across multiple schools without overloading your IT team? Wonde and Clever are two of the most […]

October 21, 2025
Stop the Sticky Notes: Bend-La Pine’s Simple, Secure Fix for Substitute Teacher AccessRobbie Faith, an instructional technology coach at Bend-La Pine Schools, successfully implemented a Clever feature to streamline secure access to digital resources for short-term substitutes, leading to more effective sub planning for teachers, increased confidence for subs, and more consistent learning for students.



















